- Home
- Meet the Team
- Log In
- Contact
- Careers
- Search
- Search Results
- Branches & ATMs
- Rates
- Log In
- About MCU
- Join MCU
- Personal Banking
- Lending
- Credit Cards
- Lending Services
- Insurance
- Member Resources
- MCU Financials
- Forms and Disclosures
- Privacy Policy
- Automated Telephone Banking
- Order New Checks
- Security & Fraud Alerts
- Privacy Notice
- Schedule an Appointment
MEMBER RESOURCES
Fraud Awareness
Protect yourself against scams and fraud. Discover essential tips and resources for staying safe online and offline.
If you suspect you've been a victim of fraud or have any questions, please don't hesitate to contact us @
1-844-MCU-NYNY
(1-844-628-6969)
Library
“S” for Security |
What We Do |
What We Don’t Do |
Dos & Don’ts for You |
Scams to Watch Out For:Social Engineering ScamsVishing ScamsPhishing ScamsSmishing ScamsSpoofing ScamsTax ScamsP2P (Peer-to-Peer) ScamsPig ButcheringQuishing ScamsSocial Media Scams |
|
What You Should Share |
||
Mobile Tips |
||
Reporting Suspected Scams |
||
Top Tip!
Think your MCU accounts have been compromised? Call the Contact Center at 1-844-628-6969. Contact Center“S” for Security
The first step in online security is checking for the lock icon and the letters https:// at the beginning of the URL in your web browser (the webpage address at the top left of your page). The letter “s” in “https” means that your connection is secure.
At MCU we employ the highest standards of security to protect your account information against Identity Theft and Fraud, including:
128-bit Secure Socket Layer (SSL) technology to encrypt your personal information, making it scrambled when transmitted over the internet, only to be decoded upon reaching your secure browser.
What We Do
MCU Online Banking requires the use of a browser that supports 128-bit encryption. Members access their online accounts by enrolling in NYMCU Online Banking and automatically starting their financial journey with robust online security.
Let’s say, as one example, that you’re making an online loan application with MCU. All loan applications are secure and encrypted, protected by multi-level data security.
Top Tip!
As of June 2022, Microsoft no longer supports the browser Internet Explorer. We strongly recommend that IE users download Microsoft Edge. Microsoft EdgeWhat We Don’t Do
MCU will never contact you by email, text message or telephone to ask you to update or verify your account information.
During your online banking login process, we will never ask you to further verify your login by inputting credit card or account information.
DO NOT respond to unsolicited text messages, email messages or telephone call asking for any account information or other private information. If you think your MCU accounts have been compromised, call the Contact Center at 1-844-628-6969.
Dos & Dont's for You
Password Strength is one of the top defenses against banking and identity fraud. When you create your password in NYMCU Online Banking, our system will rate its strength to help you create a password that is extremely hard for third-parties to guess. Other password security measures for you are:
- Don’t share your password with anybody, for any reason.
- Don’t write your password down or leave it laying around.
- Don’t reuse old passwords from old accounts.
- Don’t use the same passwords for current accounts.
- Do change your password regularly (and set a reminder so you’ll do it).
- Do answer security questions with answers others don’t know.
- Do use two-factor authentication, so you can confirm on a separate device.
- Do check any third-party access you granted and be strict about removing.
Top Tip!
Set up Account Alerts through NYMCU Online Banking and spot anything suspicious. Email or text messages will alert you when certain activity takes place.What You Should Share
Planning a trip? We’d love to hear about it if you’ll be using your MCU ATM/Debit card or Visa credit card. Sudden changes in your spending habits or patterns can trigger a security alert.
This is especially true if you’re traveling outside the state or country.
For your protection, most foreign countries are blocked. If potential fraud is detected, your card may be temporarily suspended until any questionable charge is verified.
If you’re out of town our attempts to protect you could frustrate you. Let’s avoid that. With your place of travel and departure/return dates on hand, you can contact us securely and simply as follows:
Online Banking
- Log in to NYMCU Online Banking.
- Click the “More” widget.
- Click “Message Center”.
- Send a secure message with your details.
Scams to Watch Out For
There are many ways that unscrupulous groups or individuals can gain access to your personal information, or your company information, through you. Here we’ll look at some of the top tricks that are used, often successfully, and help you to spot them, avoid them, and report them by referring to our Reporting Suspected Scams section at the bottom of this page.
Social Engineering Scams
Think charming con-artist. Social engineering happens when an individual poses as a trustworthy person and gains your time and trust. The goal is usually to obtain or compromise information about an organization or its computer systems.
This person may claim to be a new employee, researcher, repair person, or essentially anybody likely to approach you and ask for help. This person will often offer some type of “identification” to win you over.Any information given to such a person will be collected and used to aid their ultimate goal.
If the individual moves from you to somebody you recommend, your name and position would be used to gain the trust of the next victim in the chain.
Below are detailed variations of this type of scam.
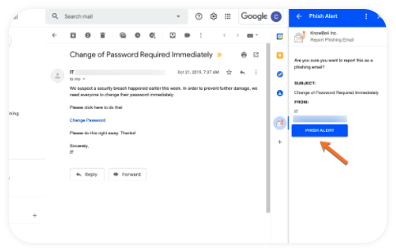
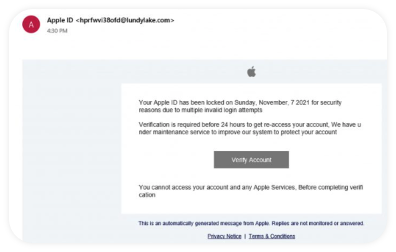
Phishing Scams
The heart of the phishing attack is the appearance of trustworthiness. It comes in the form of an email or website, which appears to represent a trustworthy individual, or an organization. Appearance is everything here and it’s increasingly difficult to spot a fake based on that alone.
You may receive an email from, for example, a “credit card company” alerting you to a problem and asking you to confirm sensitive account information. Or you could be approached by a “charity,” especially after a disaster or heavily highlighted issue in the news media.
You may even receive an email from a “friend or colleague” you trust, making it even more difficult to avoid downloading attached documents or using a link to a site from the body of the email.
Spoofing Scams
Spoofing is a type of fraud where a scammer contacts a person through phone, email, text or fax and pretends to be from a trusted source. The phone number, email address or website URL the scammer is using is disguised to look like an official communication from the organization they are pretending to be representing.
The scammer is trying to get the recipient to provide them with confidential data like passwords, account information, social security numbers, etc.
Vishing Scams
Vishing means a con enacted using voice communications. The name comes from “Voice Phishing”. Like phishing and social engineering, you are contacted by somebody who seems trustworthy. In some cases, Voice over Internet Protocol (VoIP) solutions and broadcasting services are used (or abused).
This can enable a scammer to easily spoof caller ID, thus creating trust. Defenses are often down due to trust in phone services, especially landline. In most cases, the victim receives a call from a voice message claiming to represent a financial institution.
Victims have been asked to call a number provided and enter their PIN or account information. In some cases, people claiming to be calling from Apple or Windows have informed victims that immediate action must be taken to avoid being hacked!
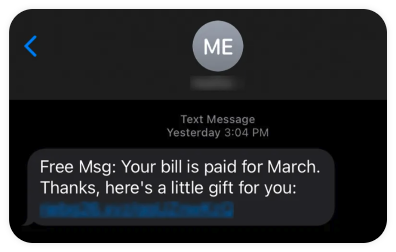
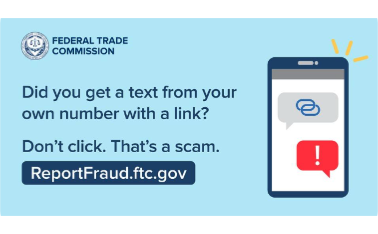
Smishing Scams
Smishing is phishing by text. Once again, a text message is sent from what appears to be a trustworthy person or organization and the victim is urged to take actions they really shouldn’t.
This type of attack is one of the most dangerous.
Due to the increasing popularity of text messaging, studies have found that people are more inclined to trust and respond to text messages of this type. According to Gartner in 2016, a whopping 98% of text messages are read, with 45% being responded to.
This brings a whole new meaning to the phrase: “Read between the lines.”
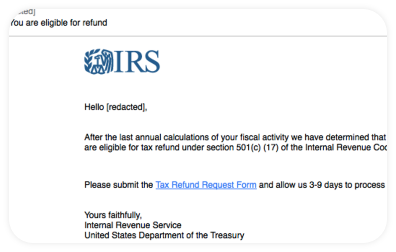
Tax Scams
Perhaps not surprisingly, tax season means high season for tax scams. As with other scams discussed on this page, being cautious when unsure is the recommended course of action. There is no shame in being scammed, because those who enact scams are, unfortunately, extremely sophisticated.
Learning their methods and what you can do to protect yourself is important. Also, reporting suspected scams supports and helps protect everybody. You can read more about that in the final section.
According to the IRS itself, tax scams come in many forms, including:
- Fake text messages.
- Social media accounts.
- Emails.
- Phone calls.
In the face of so many everyday ways to enact a scam, you should protect yourself. Below, we’ll quote directly from the IRS, so you can be certain that the IRS DOES NOT:
- Initiate unexpected contact with taxpayers by email, text messages or social media channels to request personal or financial information.
- Call to demand immediate payment using a specific payment method such as a prepaid debit card, gift card or wire transfer. The IRS does not use these methods for tax payments.
- Threaten to immediately bring in local police or other law-enforcement groups to have the taxpayer arrested for not paying.
- Demand that taxes be paid without giving the taxpayer the opportunity to question or appeal the amount owed.
- Ask for credit or debit card numbers over the phone.
- Leave pre-recorded, urgent or threatening phone messages.
- In many variations of the phone scam, victims are told if they do not call back, a warrant will be issued for their arrest. Other verbal threats include law-enforcement agency intervention, deportation or revocation of licenses.
- Criminals can fake or “spoof” caller ID numbers to appear to be anywhere in the country, including from an IRS office, which makes it difficult for taxpayers to verify the actual caller’s number.
- Fraudsters have spoofed local sheriff’s offices, state departments of motor vehicles, federal agencies and others to convince taxpayers the call is legitimate.
- Any taxpayer receiving a scam phone call should hang up immediately and not give out any information.
Businesses of all types and sizes, especially small businesses, need to be aware cybercriminals could target their businesses with scams to steal passwords, divert funds or steal employee information.
The IRS has confirmed that it continues to see instances where small businesses, including tax professionals, face a variety of identity-theft related schemes that try to obtain information to file a business tax return or use customer data for identity theft.
Businesses, including tax professionals, are encouraged to follow best practices from the Federal Trade Commission, including to:
- Use multi-factor authentication.
- Set security software to update automatically.
- Back up important files.
- Require strong passwords for all devices.
- Encrypt devices.
P2P (Peer-to-Peer) Scams
Peer-to-peer or P2P services allows for the ease in which you can send and receive money between accounts using your bank account, debit cards or standalone applications. Some of the more common P2P apps that you might be familiar with are Cash App, PayPal, Venmo, and Zelle.While P2P payments offer convenience, it’s crucial to remain vigilant as fraudsters will exploit this payment method to deceive you.
Here are some common scams to lookout for:
- Romance Scam: The scammers reach out to you via online with a fake profile seeking a romantic relationship. The interaction is typically limited to email or text messages. Once they’ve gained
your trust, they will request for you to either receive money on their behalf or for you to send them money so they have the means to travel to physically be with you. - Imposter Scam: The scammers are pretending to be someone you know or trust; usually your financial institution, a utility company or a government agency.
- Goods and Services: The scammers are posting bogus goods or services online. You will not be given an opportunity to inspect anything in person. But they will try to persuade you to pay in full or put down a deposit with a promise to deliver. Once you have sent the payment, you won’t hear from them again nor will you receive the item.
- Charitable Donation: Scammers reach out to you for donations to a fictitious charity or the impersonation of a legitimate company related to current events.
- Accidental Transfers: Someone you don’t know contacts you stating that they accidentally sent you funds by mistake and asks you to send it back. Do not follow their instructions as the
scammer is sending you stolen funds. Instead, contact the P2P service about the “error”. If you send money back to the scammer, the P2P service could take funds out of your account and hold you responsible.
What to Look Out For - Did you receive an urgent request for funds? This is a pressure tactic. Beware as scammers typically rely on this sense of urgency to get you to act now.
- There are no other payment options offered other than P2P payments.
- Does the offer sound too good to be true?
- Be on the lookout for correspondence that contain grammatical and spelling errors.
How to Protect Yourself - Do not send or accept P2P payments from someone you don’t know and trust. This includes accepting funds on someone else’s behalf.
- Treat P2P payments like cash. Never pay a seller whose goods you haven’t verified or seen in person.
- If you have the option to use a phone number or an email for a token, we recommend enrolling your phone number as a token, as emails are more easily compromised.
- Do not share your personal information or verification codes. MCU will never contact you by email, text message or telephone to ask you to update or verify your account information.
- During your online banking login process, we will never ask you to further verify your login by inputting credit card or other personal identifying information.
- Report to MCU immediately upon discovery of suspicious activity.
- Keep all records of communication related to the scam.
- Monitor your account(s) closely for additional suspicious activity.
- Enable multi factor authentication.
Report to your local law enforcement or to the FBI’s Internet Crime Complaint Center via the following link: https://www.ic3.gov/
Pig Butchering
What is Pig Butchering?
Pig butchering is a term used to describe a type of online investment fraud involving cryptocurrency. These scams are referred to as “pig butchering” as they resemble the practice of fattening a pig before slaughter. Victims in this situation are referred to as “pigs” by the scammers who leverage fictitious identities, the guise of a potential relationships and elaborate stories to “fatten up” the victims into believing they are in trusted relationships. The scammer then refer to “butchering” or “slaughtering” the victim after the victims assets are stolen.
These scams start off with some variation of social engineering. Perpetrators will go through great lengths to connect with Individuals or groups on a personal level and develop a relationship. They will target vulnerable people and introduce them to cryptocurrency; a form of digital currency. is legally traded, however frequently used in online investment scams as it is extremely difficult to trace. Opportunities will be presented to people for large returns, low risk, and fast money. The victims are directed to open an account through online investment websites controlled by the scammers. Once a trust has been built, scammers will persuade people to keep investing more money by sending small returns on fake investments and advise them to send more funds to gain larger returns. When the scammers have an idea that the victims might be aware of the scam or the victims want to withdraw funds and end the investment, the scammers will close the accounts and transfer the funds to accounts they control through various methods to make recovery near impossible.
Pig Butchering Scams:
- Wrong number scam: Victims will receive a simple text message from an unknown person assuming it’s an innocent wrong number text. Once you respond to this message with something as simple as “You’ve got the wrong number”, the scam begins. Through various social engineering tactics, the scammers will have gained your trust and access to your funds.
- Romance scam: Scammers will create profiles through dating apps or social media to establish a romantic relationship with you. On most occasions, most communication is done online or via text. What follows from this is again the intent to gain the victims’ trust and leverage the relationship.
- Spoofed domains: Scammers create pop up ads or send victims emails presenting cryptocurrency investment opportunity. The website the scammers direct you to are spoofed, meaning the web address or email belongs to a legitimate company, however the links used are to a fabricated site controlled by the cybercriminal.
What to Look Out For:
- Did you receive a message via text, or a direct message via dating sites, networking sites or on social media from an unknown person trying to reconnect with an old friend or stating that they reached you by accident? This is followed up by an attempt to build a relationship and establish trust
- Introduction to a lucrative virtual currency investment opportunity through seemingly legit websites or virtual asset service providers (VASPs).
- Is this new contact requesting access to remote into your device to assist with enrollment into “virtual currency investment” websites or requesting screenshots of the sign-up process so they can help?
- Instructions to conduct wire transfers overseas or purchase prepaid cards to purchase virtual currency
- High-pressure deadlines – member seems distressed or anxious to the timeline of a virtual currency investment opportunity. Does this offer sound too good to be true?
- Promises of greater returns – scammers may allow a victim to withdraw some of the investment to further build trust before pressuring a victim to invest more to make more
How to Protect Yourself:
By implementing these precautions, you can significantly reduce your risk of becoming a victim of pig butchering scams and other forms of financial fraud
- Verify identities and sources: Exercise caution with unsolicited contacts. Use tools and online searches to verify the identities of new acquaintances and the credibility of their investment proposals.
- Keep personal information private: Limit the personal and financial information you share online, especially with new or unverified contacts.
- Research investment opportunities: Before investing, thoroughly research the opportunity. Look for official reviews, regulatory compliance, and confirm the legitimacy of the platform.
- Consult with professionals: If an investment opportunity seems promising, consult with a financial advisor or investment professional who can provide an objective opinion.
- Use secure communication channels: When discussing financial matters, use secure, encrypted communication channels to protect sensitive information.
- Be skeptical of high returns: Be wary of any investment that promises high returns with little to no risk. Remember, if it sounds too good to be true, it probably is.
- Educate yourself on investment scams: Stay informed about common scam tactics and warning signs. Knowledge is a powerful tool against fraud.
- Report suspicious activities: If you encounter something suspicious, report it to the appropriate authorities. Your action could prevent others from falling victim.
- Ask a friend: Often, someone you know may have experienced a similar situation/scenario.
What to Do Next:
- Immediately stop communicating with the fraudster.
- Secure online access to accounts by changing passwords on bank accounts and any email addresses associated with them.
- Notify your financial institution to inform them of any financial transactions conducted involving the scammer
- Keep record of all correspondences
- Report incident to the local authorities or to the FBI’s Internet Crime Complaint Center via the following link: https://www.ic3.gov/
- Review your credit report and place fraud alerts if applicable
Quishing
What is a QR Code? How is it used?
A QR (Quick Response) code is a scan-able barcode that is read by a digital device’s camera to quickly access a webpage, data, share contact information, or even make payments. The QR code contains symbols in a two-dimensional format that instantly re-directs a user’s smart phone or device to the link embedded in the image.
What is Quishing?
Quishing is the use of fraudulent and/or deceptive QR codes in order to gain access to your device and personal data. Legitimate QR codes can sometimes be tampered with or altered to re-direct a user to a different location or to aid in a hacking attempt.
The dangers of scanning a malicious or altered QR code:
While scanning QR codes offers easier and more direct access to websites and information, it is imperative to know the source and intended action being requested. Scanning a compromised QR code could result in compromised devices, identity theft, and financial loss. Be aware of the common methods used by bad actors:
The bad actors share a message with a QR code on social media platforms, posting it in a public location or sending it through unsolicited via text messages and/or emails.
Action Required
The message will likely be enticing, offering a gift or a discount to participants. This can also be a form of social engineering, a tactic used to deceive a victim to gain control over a computer system or access your non-public information.
A criminal infects your smartphone or another electronic device with malware or other dangerous software. This software could compromise your device; access your data, and your financial institution applications.
Common places you will find an altered/ compromised QR Code:
Emails
Text messages
Social media posts/ Messages
Restaurants, Bars and in Menus
Retail Stores
On Parking meters/Mail Boxes
Mail and Delivery Packages
Part of a contest or sweepstakes
What are the Red Flags of Quishing?
Unexpected or unsolicited QR codes: Be cautious of QR codes that appear in unsolicited emails or messages, especially if they prompt you to take immediate action.
Lack of context or explanation: Be wary of codes that lack context or a credible source. Legitimate QR codes typically contain clear explanations of their purpose.
Unknown sender: Check the sender’s email address or contact information for any signs of illegitimacy, such as misspellings or unusual domain names.
Sense of urgency or pressure to react: Bad actors will often create a sense of urgency to prompt quick action or intimidate their victims. Exercise caution when viewing messages that pressure you to scan a QR code immediately.
How to protect yourself?
If available, use a secure QR code scanner: Consider using an app to add an extra layer of protection.
Know your source: Verify the legitimacy of the QR code by contacting the supposed sender through confirmed channels.
Block Spam Messages: Use email filters.
Think before you click: Don’t just scan a QR code to see what it is for.
What to do next?
- File a police report
- Keep all records of communication related to the scam
- Monitor your financial accounts closely for additional suspicious activity
- Contact your financial institutions
- Contact the Federal Trade Commission as soon as possible to report suspected Identity Theft
- Contact the three major credit bureaus and/or freeze your credit
Social Media Scams
What are Social Media Loan Scams? How do they work?
A “Social Media Loan Scam” is when someone uses social media platforms (i.e.: Facebook, Instagram, etc.) to deceive people into providing personal information or paying upfront fees for a loan that does not exist. The perpetrator(s) will create fake profiles or ads promising quick and easy loans with minimal credit checks but requiring sensitive details like bank account information in exchange. Quite often, they will advertise “advance-fee loans” to vulnerable individuals who are in debt and or looking for loans. These scammers will promise a loan, credit card and or mortgage, after you pay an advance fee – no matter what the individual’s credit history looks like.
These fraudsters typically buy marketing lists of people who have recently applied and or searched online for payday loans (short-term loans). They will target people with bad credit scores.
The dangers of social media loan scams:
In social media loan scams, a scammer poses as a lender through social media sites in an attempt to steal your money or identity. Scammers will go to great lengths to cheat people out of their hard-earned money or trick them into sharing valuable personal information. In a personal loan scam, criminals may create fraudulent loan companies or purport to be legitimate loan companies through social media platforms. These scams can be very convincing.
The following are red flag examples of information that scammers attempt to access:
· Personal identifiable information (PII). (Name, Date of Birth, Social Security Number, Home Address)
· Banking credentials (Passwords, PIN’s, usernames, account information, etc.)
How to protect yourself:
· Use extreme caution when dealing with anyone you’ve met online.
· Never share personal identifiable information.
· Never share banking credentials
· Know that legitimate loan companies do not need your online banking credentials to fund your bank account with legitimate loan proceeds.
· Research the loan company and contact them directly. It is recommended that you apply for loans through your financial institution.
· Search the “Better Business Bureau” to see if the company is registered.
What to do if you think you are a victim of a Social Media Loan Scam (or any scam)
· Contact your financial institutions
· File a police report
· Keep all records of communication related to the scam
· Monitor your bank accounts closely for additional suspicious activity
· Contact the Federal Trade Commission to report the scam
· File a complaint with the FBI’s Internet Crime Complaint Center
Mobile Tips
Staying secure while enjoying the freedom of online banking may seem like a contradiction to some. With freedom comes risk, right? No. The right steps can take you anywhere safely, so we’ve compiled our list of online banking security measures, which thankfully come in simple steps:
Add a Password to Your Phone
To prevent unauthorized access to your phone, set a password or Personal Identification Number (PIN). To set a PIN or password, go to your device settings. It is a good practice to change your password every 90 days.
Keep Your Mobile Device Up-to-Date
Your phone’s operating system software should be kept up-to-date by enabling automatic updates or accepting updates when prompted from your service provider, operating system provider, device manufacturer, or application provider. By keeping your operating system current, you reduce the risk of exposure to cyber threats.
Log Out
When you are finished at a website you are logged in to, log out instead of just closing the page. As an added security precaution, NYMCU Mobile Banking will time out after 20 minutes of inactivity.
Understand App Permissions before Accepting Them
You should be cautious about granting applications access to personal information on your phone or otherwise letting an application have access to perform functions on your phone.
Report a Stolen Smartphone
The major wireless service providers, in coordination with the FCC, have established a stolen phone database. If your phone is stolen, you should report the theft to your local law enforcement authorities and then register the stolen phone with your wireless provider.
Avoid Hot Spots
Accessing WI-FI networks that are open to the public can make your phone an easy target of cybercriminals. You should limit your use of public hotspots at locations like coffee shops or airports.Instead, use protected WI-FI from a network operator you trust or mobile wireless connection to reduce your risk of exposure, especially when accessing personal or sensitive information. Always be aware when clicking web links and be cautious if you are asked to enter account or login information.
Enroll in Touch ID or FingerPrint Login
Touch ID and FingerPrint Login allow users to login with the touch of their finger.
Download Applications from Reputable Sources
Ensure an app is legitimate before downloading it. You can check the legitimacy of an app by checking reviews, confirming the legitimacy of the app store, and comparing the app store’s official website with the app store link. Apps from untrusted sources may contain malware that, once installed, can steal information, install viruses and cause harm to your phone’s contents.
Reset before You Resell or Recycle
Your smartphone contains personal data you want to keep private when you dispose of your old phone. To protect your privacy, completely erase data off your phone and reset the phone to its initial factory settings.
Reporting Suspected Scams
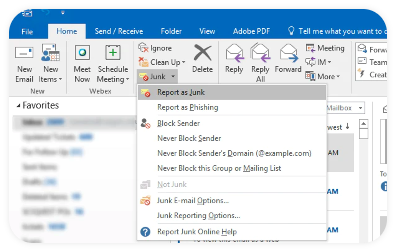
If you open an email you think is suspicious, don’t worry. Opening your emails doesn’t constitute a threat. However, clicking a link or downloading an attachment does. Never respond to suspicious emails or forward them to colleagues or friends.

 Previous Menu
Previous Menu






